Table of Contents
What Is Finney Attack?
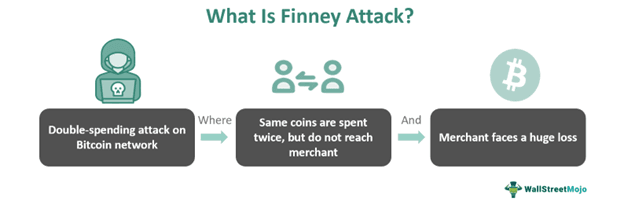
Finney attack refers to a type of double-spending attack in blockchain that occurs due to unconfirmed transactions on the Bitcoin network. The primary goal of utilizing this attack is to exploit the blockchain and earn crypto tokens by creating unauthorized transactions.
It is named after American software developer Hal Finney. In 2009, he was the first person to receive Bitcoins from Satoshi Nakamoto. Later, Finney was the first person to address the possibility of Finney's attacks on Bitcoin. These attacks may cause severe loss to the merchant.
Key Takeaways
- Finney attacks, a double-spending on the Bitcoin network, involve an individual, often a miner, attempting to spend the same coins twice without losing them.
- Named after Hal Finney, an early Bitcoin contributor, these attacks exploit the delay between transaction verification and network broadcasting.
- After a transaction is added to a block, the attacker quickly attempts to use the same coins for another transaction in a separate block, often broadcasting it immediately.
- When the network detects double spending, the coins associated with the fraudulent transaction become invalid.
- As a result, merchants may need to receive payment for goods or services.
How Does A Finney Attack Work?
Finney attacks involve attempting to spend the same coins twice by quickly initiating a transaction and then trying to spend the same coins elsewhere before the network confirms the initial transaction. While the primary goal is to execute a double spend, motivations for such attacks can vary. It's important to note that initially, both transactions may appear valid to the network until one is confirmed and the other is rejected as a double spend.
The entire process of the finney attack in blockchain occurs at the block verification stage. As miners verify the transactions, they are further eligible to be included in the blockchain. However, this stage can be crucial and sensitive when deploying a Finney attack. Some attackers may create two transactions where one recipient is the attacker. For instance, the attacker may send coins from Wallet A to Wallet B, which are owned by himself. And another transaction may include sending payment to Merchant XYZ. However, the transactions are yet to be verified by the network.
After successfully verifying the first transaction, the miner incorporates it into the block and receives cryptocurrency as a reward. Subsequently, the miner typically broadcasts the mined block to the network, including all verified transactions. Meanwhile, the attacker swiftly attempts to use the same coins for a separate transaction, aiming to double-spend them. However, before the second transaction is confirmed, the attacker broadcasts the pre-mined block containing the conflicting transaction to the network. The network rejects the conflicting transaction, but the merchant may not immediately detect this, potentially leading to mistakenly releasing goods or services to the attacker. Subsequently, upon realizing the payment has yet to be received, the merchant discovers the second transaction is invalid and remains unconfirmed by the network.
Examples
Let us look at some real-world and hypothetical examples to comprehend the concept better.
Example #1
Suppose Kevin operates an e-commerce site, selling flight tickets for the past four years. To expand his payment options, he decides to accept cryptocurrencies. However, this decision leads to a significant loss of $50,000. A week later, Kevin sells tickets to a customer named Handy Leg, who pays with cryptocurrency. Initially, Kevin receives confirmation of the payment and books the tickets. Yet, later on, he realizes that the cryptocurrency used in the transaction has become invalid.
In this hypothetical scenario, an attacker sends $50,000 worth of coins to another wallet. Although this transaction is verified and added to a block, the block containing it is not broadcast to the network. Subsequently, the attacker uses the same coins to purchase tickets from Kevin, transmitting both the coins and the pre-mined block to the network. As a result, Kevin's transaction becomes invalid, causing him a loss of 1.33 BTC.
Example #2
Let's consider a scenario where James, a miner actively involved in validating transactions on the Bitcoin network, devises a new strategy to exploit the consensus mechanism for personal gain. Instead of executing a traditional Finney attack, James employs a different approach.
James initiates a series of transactions where he sends a portion of his coins to another wallet while simultaneously making additional transactions. For example, he sends 50 BTC to Wallet B and records this transaction on the blockchain. Concurrently, he divides the remaining coins and conducts separate transactions with two different merchants.
James proceeds to purchase merchandise from an online store using 30 BTC, and the remaining coins are used to pay for a concert ticket. However, due to the nature of James' transactions, the merchants need help to utilize the coins they received for future purchases. This manipulation of the transaction process reflects James' exploitation of the network's consensus mechanism, albeit through a method distinct from a traditional Finney attack.
How To Prevent?
These attacks have existed since the origin of Bitcoin and can cause severe loss to the unaware. Hence, it is necessary to take vital steps to prevent them. Let us look at some methods:
- Increasing the confirmation time: The foremost remedy for preventing Finney attacks is using more confirmation time. The merchant must wait for a higher number of confirmations before considering the transaction as final. Usually, it is recommended to wait for six block confirmations for a transaction to be safe and secure. Only then can the transaction and associated coins be valid.
- Irreversible transactions: Another way of prevention is to look out for irreversible transactions in the network. If any transaction is irreversible, it means that these cryptos cannot be used twice. As a result, the risk of double-spending does not occur.
- Utilizing illiquid assets: Majorly hackers deploy this attack at places where the assets can be easily liquidated or exchanged for money. But, if we replace them with illiquid assets like cars, debt instruments, and others, the attackers will not attempt as such.
- Secure payment protocols: Enhancing security protocols is the most preferred method of reducing such attacks. This action is only possible at the blockchain level. Developers can improve the existing protocols, consensus mechanisms, and payment systems at the testnet phase.
- Multi-signature transactions: Blockchain protocols can deploy multi-signature protocols while transacting crypto tokens. So, if a user wishes to send a payment to Mr. B, two additional users must add their signatures for dual security.
- Deploying RBF transactions: Lastly, blockchain networks can utilize Replace-By-Fee (RBF) transactions for those that remain unconfirmed or waiting for a long time. Users can pay a higher fee and replace the transaction with a new one. Thus, the original transaction will turn invalid even if it is included in a block.
